Posts Tagged Web 2.0
The House is on fire. We don’t need no water, just some Skype.
Posted by actiancefederal in Compliance, Enterprise 2.0, New Internet, Social Networking, Trends, Unified Communications, Web 2.0, Web Security on September 15, 2011
Wow, for you naysayers out there that think the government is slow, archaic, and behind-the-times, you may have to reconsider your position. The House of Representatives has OK’d the use of Skype and ooVoo within its hallowed halls. Up to now, security concerns had impeded adoption of these popular Internet phone and video conferencing tools, respectively, but now that those concerns have been addressed, the House is ready to move forward on its plan to improve communications and transparency with its constituents.
In these tough economic times where government budgets are strapped, leveraging technology solutions that tout cost efficiencies are gaining traction. Moreover, technological enhancements and plentiful bandwidth are driving the government to look at other real-time alternatives. Applications like Skype and ooVoo allow for virtual town hall meetings, facilitate responding to constituent inquiries, and obviate the need for travel in many instances. The net effect is a fluid, cost-effective communications channel between representatives and their constituents.
Now, the House had every right to take its time in blessing the use of Skype and ooVoo. Security concerns are justified, given the abundance of horror stories involving security breaches in government and other industries as well. The problem with social media and other Web 2.0 applications is that their ubiquity opens whole new vectors for malware and other types of evil to infiltrate the corporate or government network. The proliferation of content on these types of sites is mind-boggling – photos, videos, wikis, blogs, tweets, and the list goes on and on. But, each one of these types of content can be a springboard for malware.
Given the viral nature of social media and the breadth of the social graph, it doesn’t take much for a virus to spread. A simple, innocent click on a link to your friend’s supposed Morocco vacation pictures may not yield camel pictures, but rather, expletives flowing out of your mouth when you see the Blue Screen of Death.
That’s why you see so many security software and hardware vendors in the marketplace. They’re there for a reason. Not the sexiest technology, but definitely critical to your sanity and to the long-run viability of your company, or in the case of this blog entry, the House of Representatives. Having security systems and policies in place to control the glut of Web 2.0-type applications out there (Skype and ooVoo are just two of the thousands) is downright essential.
Without granular controls of social media, instant messaging, video conferencing, and the like, safely managing that fluid communications channel between government and the constituents becomes that much more difficult. Throw into the mix potential national security implications and one can see why security breaches aren’t taken lightly in government circles.
So, bravo to the House for giving the green light to Skype and ooVoo. Now, I can Skype my congresswoman to fix that pothole in front of my driveway.
Embracing Social Business
Posted by ASocialNomad in Enterprise 2.0, New Internet, Social Networking, Trends, Uncategorized, Web 2.0 on September 12, 2011
Not long ago we blogged about the proliferation of mobile devices being used by the next generation of consumers to access the new Internet and its impact on financial services. This was the topic of a recent webinar and accompanying white paper from Forrester Research, and it’s a growing concern for all businesses – how to create safe, effective marketing programs using the latest social media platforms that drive business in a measureable way.
I recently chatted with Erin Traudt, Research Director at IDC and their resident guru on all things social (Michael Fauscette , you’ll have to forgive me, I’m not lessening your guruness with that comment 😉 ) , about the marketing capabilities we recently introduced in Socialite Engage. Erin pointed us to two public Insight reports on the IDC web site that define a new kind of Social Business Framework:
“The democratization and socialization of media through the social web has turned anyone into a publisher, reporter and/or critic – subsequently redefining influence. The social customer, employee, supplier and partner each have a voice and the means to use that voice at scale. And people are listening.”
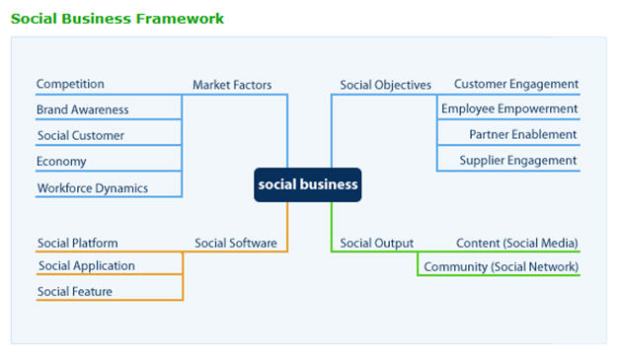
Source: IDC
IDC’s definition of social business is companies using emerging technologies (like Web 2.0 and social media) to make cultural and organizational changes to drive business. According to the IDC report, “Social Business Framework: Using People as a Platform to Enable Transformation,” there are four steps to implementing a social business:
- Identify the market factors driving the need for change to social business. Market factors can include such things as competition, brand awareness, customer behavior, and the economy,
- Recognize social objectives you want to accomplish and why they matter. Social objectives are linked to business goals and include such elements as customer engagement, employee empowerment, partner enablement, and supplier engagement.
- Establish social outputs to support those social objectives. These are the mechanisms you use to share, such as tweets and Facebook posts. Content creation democratizes the process so customers and partners can join the conversation, and you have to consider your community as part of social output, i.e. those individuals who are connected in some way, ideally around your brand.
- Determine the platforms and applications you need to achieve your desired social outputs. These are the software tools that you need to build, deploy, and manage social applications, such as Jive, Lotus Connections, and Facebook, and, of course, tools like Socialite Engage.
As part of your social business strategy, you need to adopt business tools that measure the impact of social output and social media platforms. According to the IDC Insight report Determining the Value of Social Business ROI: Myths Facts and Potentially High Returns, most organizations don’t even know how to calculate ROI for traditional projects, let alone for social business. Identifying metrics to monitor social media engagement allows companies to optimize customer acquisition, decrease customer churn, and create upsell and cross sell opportunities. But to do that, you need to be able to gain control of your social media program and measure the effectiveness and ROI of social media programs.
According to the latest Social Business Survey from IDC, there are five primary reasons that end users use social media as part of social business:
- Acquire knowledge and ask questions;
- Share knowledge and contribute ideas;
- Communicate with customers;
- Create awareness about company product or service; and
- Communicate with internal colleagues.
As part of your social business strategy, you need to think of the impact your social business program has on your social media audience in terms of:
- Reach: How extensive is your online footprint and are you being effective at building an online following?
- Impact: What part of your online community is active, pay attention to your products and messages, and influencing others?
- Yield: How much revenue or new business can you link to active members of your social media community?
These are all factors we took into consideration in when we designed Socialite Engage. We understand that for certain industries it’s essential to not only promote conversation with preapproved content, but to understand how that content performs in achieving social business goals, and which channels are yielding the desired results.
As a firm, as a business, to gauge the effectiveness of a social business initiative, you have to be able to track aggregated engagement across different social media platforms, determine who your key influencers are, and how those influencers are affecting your bottom line. And that’s what we’ve done with Socialite Engage. We’ve designed the means to identify and track key connections into Socialite Engage, and ways to track their influence. We’ve also built in analytics to determine how those connections are affecting business, which channels and messages are having the greatest impact on sales, lead generation, or whatever initiative you have determined will drive your social business.
Embracing social business isn’t just about improving customer relations and increasing sales, it’s about changing the very DNA of your people and the organization. Developing a social business strategy means empowering your people, your customers, your partners, and your suppliers with new tools that can impact your brand and reputation, as well as your bottom line. As a result, you need new tools to monitor the conversations and measure their impact. That’s what our next generation of social business engagement tools is all about.
Follow my experiences in beta testing Socialite Engage – as I endeavor to change the social behavior and the results of social collaboration of Actiance team members, partners and customers. You can watch it all here – at blog.actiance.com (or follow us on Twitter @SarahActiance and @Actiance)
Social Media and Cloud Security, are they on the new Federal CIO’s radar?
Posted by actiancefederal in Malware, Social Networking, Unified Communications, Web 2.0, Web Security on August 8, 2011
Last week, it was announced that Steven VanRoekel would be replacing Vivek Kundra as the CIO at the Office of Management and Budget (OMB). It’s a high-profile position that essentially puts VanRoekel in charge of the federal government’s IT budget – currently about $80 billion a year. A tidy sum of money.
So, as VanRoekel assumes his new role, all eyes will be focused on how he handles the projects he’s inheriting from Kundra as well as new initiatives. Of the former, issues such as data center consolidation and the “cloud” are top-of-mind. Recently, much of the buzz, both in the government and in the private sector, has revolved around Web 2.0 and social media. However, they’re just two components of an overall security strategy.
VanRoekel must also take into consideration other types of application that factor into a comprehensive cybersecurity strategy. These days, hackers are pretty sophisticated and are quite adept at exploiting encrypted traffic to pass along viruses or other types of malware. For instance, unified communications (UC) platforms, such as Jabber, Microsoft OCS and Lync, and IBM Sametime, all enable federation, which is the ability to communicate with others who are not members of your UC community. The danger here is federating with outside networks that may present unknown risks, like viruses, hackers, enemies mining for confidential information, etc.
The same analogy holds for the “cloud” initiative. Cloud computing is all the rage, but there’s no shortage of companies and government agencies that are incredibly leery of turning over key computing processes and applications to the cloud. Security is almost always the first issue mentioned when talking to skeptics of the cloud. Multi-tenancy (i.e., sharing physical appliances that have been logically partitioned), data storage off-premises, and the relatively short history of this computing paradigm send shivers down the spines of the most experienced IT practitioners.
With the Internet being a global resource, the potential scope of security breaches is immense. Sophisticated hackers might reside in the US, China, Russia, Iraq, North Korea; you just never know. It is under this backdrop that VanRoekel will have to drawn upon his experience in the private and public sectors to devise a strategy addressing all of these security concerns. A daunting challenge for sure, but absolutely attainable, given today’s technology.
Wouldn’t you agree?
Are you socially mobile or stuck in a time lapse?
Posted by ASocialNomad in Compliance, New Internet, Social Networking, Trends, Unified Communications, Web 2.0 on May 3, 2011
Most social media interaction relies on a fairly immediate response. A tweet has a half life of 3 hours for instance. Whether it’s responding to a customer query, discussing the latest piece of industry news with a partner or just a bit of friendly banter with colleagues, joining in the conversation an hour later can be an opportunity missed. It’s one of the reasons so many of us take our mobile or cell phone wherever we go. I might only be the other side of the office, but I can still respond instantly to something pertinent, without having to walk back to my desk.
Mobility has become an important part of our lives, but it has also added a complexity to the IT aspect of controlling data. A couple of years ago most enterprises standardised on PCs, laptops and mobiles. Today, users want to be able to choose not just the device that helps them do their job the best, but also the one they feel most comfortable using. Some prefer proper keyboards on their mobile, others like electronic; iPads are really popular with sales guys doing a lot of presentations, hated by others for their lack of true multi-tasking. Users even consider the personal aspects of their devices – can they continue reading the latest thriller on the commute to work, video conference with their family when away from home.
The end result for the poor IT guy is that he has to control and record information coming in and going out of the network through a myriad of devices. It’s one of the reasons we developed our technology to focus on the data stream to the social media application, not the method of communication. We already provide full support for recording conversations on Facebook and LinkedIn regardless of device and will be extending this to include Twitter in May.
However, providing support via a direct connection to the API of the social network is only half the story. It won’t surprise you to learn that social media sites are constantly updating their offering, but it may surprise you to know how many changes are made on a weekly basis that directly affect how third party systems such as those provided by Actiance function. The top three sites Facebook, LinkedIn and Twitter average around twenty changes a week, though for a couple of weeks in March they nearly topped forty. Some are minor changes or tweaks, others have a significant impact in the way data is handled.
Fortunately, our close relationship with the major social networking sites means that we are frequently aware of changes ahead of time and can easily make any necessary changes to our own technology in response. In addition, the constant moving of goal posts is nothing new to Actiance. Our heritage in dealing with the instant messaging networks from way back when in the early 2000’s where the introduction of new networks and protocol changes were profuse has enabled us to develop processes that enable our research and technical team to react swiftly.
As the workforce becomes more mobile, the problem of different devices isn’t going to go away. The mobile phone was once touted as being the de-facto communications tool, but the impact of tablets has shown that this might not be the case. I can’t predict what I’ll be using in the future to communicate with customers, partners and colleagues, but I do know that a point solution for devices or specific applications to enable it isn’t the long term answer. A scalable platform that enables the secure, compliant use not just of social media, but UC and Web 2.0 is.
And the award goes to…..
Posted by ASocialNomad in Compliance, FINRA, New Internet, Social Networking, Unified Communications, Web 2.0, Web Security on March 30, 2011
In the last couple of weeks we’ve been informed that our products have been shortlisted for not just one, not two, not three, but four leading industry awards (yes really!) – two of them related to Financial Services and two awards covering everyone’s darling, Social Media. This got me thinking about how modern communication tools such as UC, Social Media and Web 2.0 have completely infiltrated our working lives and the breadth and depth of platform required to enable their secure use.
In an average day I use nearly a dozen different mediums to communicate with colleagues, partners and customers including Microsoft OCS, IBM Lotus Sametime, Skype, Twitter, LinkedIn, Facebook, Quora, Blackberry Messenger and Cisco Webex. I use my iPhone, my Blackberry, my iPad, my laptop. In the past month, I’ve connected and communicated at 37,000 feet, on a cruise ship off the coast of Cuba, Costa Rica and (shame on me), even in the office. Face it, if there’s a way of connecting with the internet…I guess I’ll find it. Equally, if I worked directly in a Financial Services organization – like many of our customers – then I would probably also be adding something like Thomson Reuters Messenger or Bloomberg to the list.
You might be wondering how on earth do I find the time to work – but that’s the point, virtually everything I do on these networks helps me to do my job. But it’s also interesting that what I use has changed too. Twelve months ago I wasn’t using Facebook for chat much and I didn’t have an account on Quora, I’d certainly not Skyped at 37,000 feet, nor had I SMS’d while traversing the Panama Canal.
The other weekend I co-hosted a conference workshop for compliance officers in Utilities organizations on how to develop a social media policy. After protracted discussions about how the organizations attending use social media and considering some of the pitfalls – including my question du jour “how do you comply with retention of records on your twitter account?” that always gets the room buzzing – the group split up into teams to draft a social media policy that would work for them.
It’s almost a guarantee that somewhere in the policy specific networks, normally Facebook, will be mentioned. But in just the same way you can’t spare the time to rewrite your policy every time a new social network becomes popular, neither can you afford to update your IT controls either. Not to mention the fact that there are thousands of social networks available that may not be popular, but still have a considerable amount of users that might just be your employees. So looking at the bigger picture isn’t just important, it’s imperative.
Being able to secure, manage and meet compliance duties requires a platform that offers breadth and flexibility in adapting to the changing world we work in. I can’t claim to know what tomorrow’s hot favorite communications tool may be, but I work with a team of people who do know how to spot them and who also know how to manage them . Our Actiance Security Labs live and breathe social networks and Web 2.0 applications and track, monitor and provide management capabilities on a daily, if not hourly basis.
I’m probably not going to meet fellow brit Colin Firth (rats) over the next three weeks and my acceptance speech, should we win (again), certainly won’t be as polished as his, but I will be attending the Oscar equivalent in the IT security world, SC Magazine’s award ceremony. If you’re there, come over and say hi – I promise not to try out my question du jour.
Financial Sector Technology – Most innovative Solution of the Year – Socialite
SC Awards – Information Security Product of the Year – USG
SC Awards – Best security Solution in Financial Services – Vantage
Network Computing – New Product of the Year – Socialite
Can I get me a lil’ context with my data, please?
Posted by ASocialNomad in Compliance, Enterprise IM, Social Networking on March 29, 2011
We all know there’s a glut of information out there, what with all the social media sites, instant messaging (IM) networks, and unified communications platforms (think Microsoft OCS and IBM Sametime) being used to facilitate communications, so it should come as no surprise that making sense out of that mountain of data is no small feat.
This is the quandary many organizations face today. They’re capturing all this data but are having a difficult time organizing it into actionable data (e.g., analyzing customer buying trends, market opportunities, etc.). Many technology solutions today can capture social media content like Facebook Wall posts, LinkedIn status updates, and tweets, but nearly all of them capture only the individual post or tweet itself. When exported out to an archiving platform, such as the popular Symantec Enterprise Vault, there’s nothing but headaches for eDiscovery and legal folks, trying to piece together related tweets and Facebook posts scattered throughout an archive.
What really separates the “men” from the “boys” is not only being able to capture the data in context, but also display that context in full when retrieving content for eDiscovery, regulatory, or legal purposes. Capturing data in context means not just capturing a single “missive,” but capturing the entire stream of messages posted throughout the day in a single, simple, easy–to-read transcript. This simplifies reviewing by leaps and bounds. It also makes for a more fluid eDiscovery process as legal teams, both in-house and law firms, can more easily find the information they’re looking for and, in turn, more quickly determine if a piece of data is relevant or not. At the end of the day, man-hours and legal costs are driven down dramatically, and employee productivity is maximized.
Socialite from Actiance is one such platform that can capture data in context. Capturing content posted to sites like Facebook, LinkedIn, and Twitter and then being able to present it in transcript format makes it not only much easier for end users to find what they need and determine its relevance, but also shows the original message in its true format. You can liken it to the ol’ “quality vs. quantity” debate: what good is archiving a million different Facebook posts if you can’t make sense of it?
As the Web 2.0 and social media train screams along at breakneck speed, the chaos that data can become will only get worse and the need for that “calming” influence becomes more pronounced. Socialite brings order to that chaos.
Keep It Simple, Stupid
Posted by nleong in Application Filtering, Compliance, Employee Behavior, Enterprise 2.0, Enterprise IM, Malware, Unified Communications on February 24, 2011
We’ve all heard this saying before and it’s easy to get lost in the bewildering array of communications channels available to us. There’s the usual email, instant messaging networks (Yahoo!, Google Talk), peer-to-peer networks (Skype), enterprise IM applications (IBM Sametime, Microsoft Lync/OCS), and social networks (Facebook, Twitter). And these are just the big boys. There are literally thousands of IM, P2P, and social networks, in addition to those listed above.
To give you an idea of the bevy of tools out there, the US Department of Agriculture (USDA) uses over 21 different email systems, but they’ve recently decided to award Microsoft a contract to provide cloud-based email, Web conferencing, IM, and collaboration solutions. Similarly, the US General Services Administration (GSA) awarded an email contract to Google. What this goes to show is that messaging in large organizations (in this case, it’s the government) is starting to move to the cloud as companies look for ways to streamline their messaging systems, improve efficiency, and cut costs.
What with all these communications options available to end users, it’s all too common for folks to use Facebook, Yahoo!, or Skype while they’re at work on company-issued computers. Oftentimes, individuals use a combination of Web 2.0 (think Facebook or Skype) and enterprise (think Microsoft Communicator or Cisco Jabber) applications. The problem with doing so is that it opens up new vectors for malware to invade the corporate network. In other words, there are far more avenues for evil to infiltrate the corporate network these days than ever before.
Thankfully, platforms like Actiance Vantage make it easier to manage the proliferation of communications tools within the enterprise. From blocking virus attacks to managing file transfers to logging and archiving of all IM activities, Vantages provides end-to-end security and compliance coverage for an organization’s unified communications.
We can all learn a lesson from the government contracts cited above. Long ridiculed for being the poster child of bureaucracy and antiquated computer systems, it must be saying something to have two large agencies moving their communications applications to the cloud. Looks like the US government has taken heed of that old KISS principle after all.
Social Media Added to Advertising Regulatory Body Remit
Posted by actiance in Compliance, Electronically Stored Information (ESI), Enterprise 2.0, New Internet, Social Networking, Web 2.0 on September 12, 2010
In what is expected to be the beginning of a long list of advertising regulatory bodies around the globe, the UK’s Advertising Standards Authority (ASA) has announced changes to come into force next year that will see organizations using social media as a form of advertising firmly in the ASA firing line.
The ASA is the regulatory body for the CAP Code, the rule book governing the content and placement of non-broadcast marketing communications in the UK. Currently, the section covering online material only covers paid-for advertisements and sales promotions, but the digital code is being extended to include “other marketing communication….on their own websites, or other non-paid space online under their control.”
Social media sites are now a natural extension of the way many marketing departments communicate with prospects, customers and partners. Whether it’s launching a new product, letting people know about latest offers and even recalls, Facebook, LinkedIn and Twitter offer an easy and effective way to connect. But its casual conversational nature can also make it easy to cross boundaries into mis-selling or forgetting social responsibility such as health warnings.
Given the large number of different social networks and Web 2.0 applications, the majority of which have no native controls included to aid regulation, keeping track of social media conversations for a large marketing department will undoubtedly present some problems.
However, the productivity benefits and new business opportunities that organizations are already achieving by embracing social media, means that companies must implement new solutions to control it or face losing out to the competition.
Companies worried about the ASA guidelines should take a look at FaceTime’s Socialite.
Yesterday’s solution doesn’t address today’s issues
Posted by actiance in Compliance, Enterprise 2.0, Enterprise IM, New Internet, Public IM, Social Networking, Unified Communications, Web 2.0 on December 2, 2009
Normal
0
false
false
false
MicrosoftInternetExplorer4
/* Style Definitions */
table.MsoNormalTable
{mso-style-name:”Table Normal”;
mso-tstyle-rowband-size:0;
mso-tstyle-colband-size:0;
mso-style-noshow:yes;
mso-style-parent:””;
mso-padding-alt:0cm 5.4pt 0cm 5.4pt;
mso-para-margin:0cm;
mso-para-margin-bottom:.0001pt;
mso-pagination:widow-orphan;
font-size:10.0pt;
font-family:”Times New Roman”;
mso-ansi-language:#0400;
mso-fareast-language:#0400;
mso-bidi-language:#0400;}
Today’s guest blogger is Eric Young. Eric is FaceTime’s Sr,
Director of Field Services, and works with FaceTime customers to
implement leading edge security and compliance solutions for Unified
Communications and Web 2.0. Eric’s
worldwide role gives him an insight into the global requirements of
organizations implementing real time communications technologies to enable
their businesses and works closely with our product team to ensure that
FaceTime solutions remain at the forefront of the industry.
Yesterday’s solution doesn’t address today’s issues.
I was onsite with a customer
recently completing our fifth competitive replacement within the Fortune
400 in the past 6 months. As the customer was detailing all of the
requirements the previous solution did not satisfy, it made me wonder, how are
other customers of these competitors feeling they are operating in a compliant
fashion?
If you, as a compliance officer
or legal counsel, cannot make sense of a group chat conversation,
cannot actually view the content of a blocked message, or can’t see what
folks are trying to post to a social networking site; how can you
possibly defend your organization from SEC fines or from a
lawsuit in a court of law?
Security
technologies evolve quickly, especially in the area of real-time communications
– but the adoption of tools like Unified Communications, Instant Messaging and
social media has grown exponentially – in many cases even without the knowledge
of either IT or compliance.
Regulation
and compliance changes too, with the times.
Most recently I’ve seen FINRA starting to address the issue of social
media and issuing guidelines to member organizations and individuals on how
usage should be treated.
We all understand there is a big
difference between “logging” and “being compliant” but
knowing there are still some banks and other highly regulated companies using these
legacy solutions that were designed for technology of a few years back, it begs
the questions: What are the minimum requirements for security and
compliance for Unified Communications, Instant Messaging and Social Media?
And,
what are you doing about dealing with emerging technology?
Guest Blogger: Damon Martin, of SKT on Unified Comms & Web 2.0
Posted by actiance in Enterprise 2.0, New Internet, Social Networking, Unified Communications, Web 2.0 on November 25, 2009
Damon Martin, takes a primary role in the development of technical and sales direction for
SKT, a national Unified Communications consulting firm based in the central
US. Damon executes consulting practices and sales methodologies developed to
ensure organizations realize the promise of Unified Communications.
Here, Damon discusses what’s changed in the workplace – and what’s becoming more relevant.
For
many of us that have been consulting on Unified Communications for
years it is hard to see the transformations when they are happening. I
remember talking to organizations about CTI when the idea that your
computer could talk to your PBX was bleeding edge. There has been an
enormous amount of discussion in the past year about Unified
Communications and its business impact. An interesting transition for
me has been that I don’t find myself answering the question “What is
Unified Communications?” anymore. Instead, I find myself talking to
organizations about what Web 2.0 and social networking mean to their
business. The reality is that those questions are a natural progression
of the dialog. There is an inherent link between Facebook, Twitter,
LinkedIn and other social networking tools and Unified Communications.
What is changing in the workplace?
There is
awareness within today’s workplaces that we have to find ways to become
more productive. The effects of today’s economic environment and
acceptance of the “new normal” have allowed us to see the workforce
output that is expected for information workers at our companies. That
productivity is fueled by an increasing demand for a collaborative
working culture. There are several trends that are emerging in the new
workplace:
- Unwillingness to return to previous employment levels
- Demands for higher productivity from information workers
- Elimination of organizational layers
- Increasing expectations for staff to take on a variety of roles and responsibilities
There is an interesting phenomenon of the new workforce; workers are
finding an environment where they are being forced to collaborate with
others at a much higher degree than was required previously. This
pressure has a logical conclusion that we are seeing play out in many
organizations:
- Workers need to collaborate quickly and effectively and today’s
phones and email are not fast enough with most communications resulting
in a voicemail or replies hours later. - Workers have become accustomed to instant access to friends and
family with text messages, Facebook, Twitter and instant messaging.
The result is that workers have a desire and need to use
collaboration tools. If we look at Unified Communications as a tool
and explore its ability to add business value by driving collaboration,
we can start to understand how social networking is an indication of
the willingness of our teams to embrace Unified Communications and
Collaboration.
Why is Web 2.0 relevant?
The key to the adoption
of Unified Communications in the workplace is embracing it as a
collaboration tool. The question about whether people can use social
networking tools to collaborate has been answered by the prolific
growth of tools and social network sites. The burden now is on
solutions providers and vendors to help executives at companies
understand how to leverage a Unified Communications platform to provide
a tool-set. Businesses need to continue growing productivity without
returning to the staffing levels they that drove up costs. We hear the
question “how can we get our staff to embrace Unified Communications”.
The key is to understand that they already have by tweeting feedback at
a trade show or posting pictures of grandchildren on Facebook. The
vendors are doing a good job of showing demos of how Unified
Communications works to IT departments. In the interim, workers are
finding ways to collaborate because they have to stay competitive and
provide the output that is expected in today’s workplace.
Conclusion
It is time for the technology
departments to accept that Unified Communications is not something that
can be migrated to over time or tested for small user groups.
Businesses are not going to back away from demands for increasing
productivity. Workers have realized that collaborative communication
is the way to make productivity sustainable. We have to work to help
organizations understand that Unified Communications and Collaboration
(UCC) is where the consumer acceptance of social networking and the
business software for Unified Communications come together.
Damon originally posted this blog entry at the SKT Blog earlier in November 09. You can follow Damon on Twitter.